What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-01-21 16:48:03 | A week in security (January 14 – 20) (lien direct) |
 A roundup of last week's security news from January 14 to 20, including APT10, Fallout EK, Colllection 1 data, Youtube challenges, hosting malicious sites and a Fortnite security flaw.
Categories:
Security world
Week in security
Tags: APT10ArsTechnicaBleepingComputerCoinDeskcollection 1cryptopiacve-2019-0543DASFallout EKfortnitegarminGarmin watchhostingHTTPSoregonpowershellPowerShell Team BlogSC Mediashutdowntelegramthreadxyoutube
(Read more...)
A roundup of last week's security news from January 14 to 20, including APT10, Fallout EK, Colllection 1 data, Youtube challenges, hosting malicious sites and a Fortnite security flaw.
Categories:
Security world
Week in security
Tags: APT10ArsTechnicaBleepingComputerCoinDeskcollection 1cryptopiacve-2019-0543DASFallout EKfortnitegarminGarmin watchhostingHTTPSoregonpowershellPowerShell Team BlogSC Mediashutdowntelegramthreadxyoutube
(Read more...)
|
APT 10 | |||
| 2019-01-16 17:00:00 | The Advanced Persistent Threat files: APT10 (lien direct) |
 While security companies are getting good at analyzing the tactics of nation-state threat actors, they still struggle with placing these actions in context and making solid risk assessments. So in this series, we're going to take a look at a few APT groups, and see how they fit into the larger threat landscape-starting with APT10.
Categories:
Cybercrime
Hacking
Tags: advanced persistent threatadvanced persistent threatsaerospaceAPTAPT10APTschinaChinese Ministry of State SecurityconstructionengineeringFireEyeMSSPlugXPoison Ivyscanboxsogutelecomsthreat actors
(Read more...)
While security companies are getting good at analyzing the tactics of nation-state threat actors, they still struggle with placing these actions in context and making solid risk assessments. So in this series, we're going to take a look at a few APT groups, and see how they fit into the larger threat landscape-starting with APT10.
Categories:
Cybercrime
Hacking
Tags: advanced persistent threatadvanced persistent threatsaerospaceAPTAPT10APTschinaChinese Ministry of State SecurityconstructionengineeringFireEyeMSSPlugXPoison Ivyscanboxsogutelecomsthreat actors
(Read more...)
|
Threat | APT 10 | ||
| 2019-01-16 00:52:03 | “Stole $24 Million But Still Can\'t Keep a Friend” (lien direct) | Unsettling new claims have emerged about Nicholas Truglia, a 21-year-old Manhattan resident accused of hijacking cell phone accounts to steal tens of millions of dollars in cryptocurrencies from victims. The lurid details, made public in a civil lawsuit filed this week by one of his alleged victims, paints a chilling picture of a man addicted to thievery and all its trappings. The documents suggest that Truglia stole from his father and even a dead man -- all the while lamenting that his fabulous new wealth brought him nothing but misery. | APT 15 | |||
| 2018-12-21 16:30:11 | Managing Burnout (lien direct) |  This is not strictly an information security post, but the topic likely affects a decent proportion of my readership.Within the last few years I experienced a profound professional "burnout." I've privately mentioned this to colleagues in the industry, and heard similar stories or requests for advice on how to handle burnout.I want to share my story in the hopes that it helps others in the security scene, either by coping with existing burnout or preparing for a possible burnout.How did burnout manifest for me? It began with FireEye's acquisition of Mandiant, almost exactly five years ago. 2013 was a big year for Mandiant, starting with the APT1 report in early 2013 and concluding with the acquisition in December.The prospect of becoming part of a Silicon Valley software company initially seemed exciting, because we would presumably have greater resources to battle intruders. Soon, however, I found myself at odds with FireEye's culture and managerial habits, and I wondered what I was doing inside such a different company.(It's important to note that the appointment of Kevin Mandia as CEO in June 2016 began a cultural and managerial shift. I give Kevin and his lieutenants credit for helping transform the company since then. Kevin's appointment was too late for me, but I applaud the work he has done over the last few years.)Starting in late 2014 and progressing in 2015, I became less interested in security. I was aggravated every time I saw the same old topics arise in social or public media. I did not see the point of continuing to debate issues which were never solved. I was demoralized and frustrated.At this time I was also working on my PhD with King's College London. I had added this stress myself, but I felt like I could manage it. I had earned two major and two minor degrees in four years as an Air Force Academy cadet. Surely I could write a thesis!Late in 2015 I realized that I needed to balance the very cerebral art of information security with a more physical activity. I took a Krav Maga class the first week of January 2016. It was invigorating and I began a new blog, Rejoining the Tao, that month. I began to consider options outside of informations security.In early 2016 my wife began considering ways to rejoin the W-2 workforce, after having stayed home with our kids for 12 years. We discussed the possibility of me leaving my W-2 job and taking a primary role with the kids. By mid-2016 she had a new job and I was open to departing FireEye.By late 2016 I also realized that I was not cut out to be a PhD candidate. Although I had written several books, I did not have the right mindset or attitude to continue writing my thesis. After two years I quit my PhD program. This was the first time I had quit anything significant in my life, and it was the right decision for me. (The Churchill "never, never, never give up" speech is fine advice when defending your nation's existence, but it's stupid advice if you're not happy with the path you're following.)In March 2017 I posted Bejtlich Moves On, where I said I was leaving FireEye. I would offer security consulting in the short term, and would open a Krav Maga school in the long-term. This was my break with the security This is not strictly an information security post, but the topic likely affects a decent proportion of my readership.Within the last few years I experienced a profound professional "burnout." I've privately mentioned this to colleagues in the industry, and heard similar stories or requests for advice on how to handle burnout.I want to share my story in the hopes that it helps others in the security scene, either by coping with existing burnout or preparing for a possible burnout.How did burnout manifest for me? It began with FireEye's acquisition of Mandiant, almost exactly five years ago. 2013 was a big year for Mandiant, starting with the APT1 report in early 2013 and concluding with the acquisition in December.The prospect of becoming part of a Silicon Valley software company initially seemed exciting, because we would presumably have greater resources to battle intruders. Soon, however, I found myself at odds with FireEye's culture and managerial habits, and I wondered what I was doing inside such a different company.(It's important to note that the appointment of Kevin Mandia as CEO in June 2016 began a cultural and managerial shift. I give Kevin and his lieutenants credit for helping transform the company since then. Kevin's appointment was too late for me, but I applaud the work he has done over the last few years.)Starting in late 2014 and progressing in 2015, I became less interested in security. I was aggravated every time I saw the same old topics arise in social or public media. I did not see the point of continuing to debate issues which were never solved. I was demoralized and frustrated.At this time I was also working on my PhD with King's College London. I had added this stress myself, but I felt like I could manage it. I had earned two major and two minor degrees in four years as an Air Force Academy cadet. Surely I could write a thesis!Late in 2015 I realized that I needed to balance the very cerebral art of information security with a more physical activity. I took a Krav Maga class the first week of January 2016. It was invigorating and I began a new blog, Rejoining the Tao, that month. I began to consider options outside of informations security.In early 2016 my wife began considering ways to rejoin the W-2 workforce, after having stayed home with our kids for 12 years. We discussed the possibility of me leaving my W-2 job and taking a primary role with the kids. By mid-2016 she had a new job and I was open to departing FireEye.By late 2016 I also realized that I was not cut out to be a PhD candidate. Although I had written several books, I did not have the right mindset or attitude to continue writing my thesis. After two years I quit my PhD program. This was the first time I had quit anything significant in my life, and it was the right decision for me. (The Churchill "never, never, never give up" speech is fine advice when defending your nation's existence, but it's stupid advice if you're not happy with the path you're following.)In March 2017 I posted Bejtlich Moves On, where I said I was leaving FireEye. I would offer security consulting in the short term, and would open a Krav Maga school in the long-term. This was my break with the security |
APT 1 | |||
| 2018-12-21 15:51:02 | Industry Reactions to U.S. Charging APT10 Hackers: Feedback Friday (lien direct) | The United States, United Kingdom, Canada, Australia, New Zealand and Japan have pointed the finger at China for sophisticated cyberattacks launched by a threat group known as APT10 against organizations around the world. The U.S. | Threat | APT 10 | ||
| 2018-12-21 15:44:05 | Five other countries formally accuse China of APT10 hacking spree (lien direct) | Australia, Canada, Japan, New Zealand, and the UK also point the finger at the Beijing government. Germany expected as well. | APT 10 | |||
| 2018-12-21 09:55:03 | Historic APT10 Cyber Espionage Group Breached Systems in Over 12 Countries (lien direct) | A well-known hacking group linked with China's intelligence and security agency has been pilfering secrets for over a decade from organizations in at least 12 countries, from a diverse range of industries. [...] | APT 10 | |||
| 2018-12-21 07:24:01 | \'Five Eyes\' Nations Blame China for APT10 Attacks (lien direct) | The United States, United Kingdom, Canada, Australia and New Zealand officially blamed China on Thursday for the cyberattacks launched by a threat group known as APT10 against organizations around the world. | Threat | APT 10 | ||
| 2018-12-20 23:45:03 | US Indicts Two Chinese Government Hackers Over Global Hacking Campaign (lien direct) | The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous companies and government agencies in a dozen countries.
The Chinese nationals, Zhu Hua (known online as Afwar, CVNX, Alayos and Godkiller) and Zhang Shilong (known online as Baobeilong, Zhang Jianguo and Atreexp), are believed to be members of a state-sponsored
|
APT 10 | |||
| 2018-12-20 19:38:02 | U.S. Indicts China-Backed Duo for Massive, Years-Long Spy Campaign (lien direct) | The homeland security implications are significant: the two, working with Beijing-backed APT10, allegedly stole sensitive data from orgs like the Navy and NASA. | APT 10 | |||
| 2018-12-20 16:38:00 | US charges two Chinese nationals for hacking cloud providers, NASA, the US Navy (lien direct) | The two Chinese nationals were members of the infamous APT10 cyber-espionage group, DOJ said. | APT 10 | |||
| 2018-12-20 14:00:00 | Let\'s Chat: Healthcare Threats and Who\'s Attacking (lien direct) |
Healthcare is under fire and there’s no sign of the burn slowing.
Look, it’s no secret that hackers have been targeting hospitals and other healthcare providers for several years — and probably no surprise that healthcare is one of the top target industries for cybercrime in 2018. In the US alone, in fact, more than 270 data breaches affecting nearly 12 million individuals were submitted to the U.S. HHS Office for Civil Rights breach portal (as of November 30, 2018). This includes the likes of unauthorized access or disclosures of patient data, hacking, theft of data, data loss and more.
Bottom line, if you’re tasked with protecting any entity operating in the healthcare sector, you’re likely experiencing some very sleepless nights — and may just need a doctor yourself.
So . . . who’s wreaking all this havoc and how? According to AlienVault Labs, opportunistic ransomware is still a preferred method of attack. However, researchers are reporting a rise in the number of targeted ransomware attacks in the healthcare sector. These attacks are often backed by organized criminals who see opportunities for making money from healthcare providers and other similar entities who must protect and keep assets, systems, and networks continuously operating.
One such criminal group operating the SamSam ransomware is thought to have earned more than $5 million dollars by manually compromising critical healthcare networks (see below for more info). The group behind SamSam has invested heavily in their operations (likely an organized crime syndicate) and has won the distinction of being the subjects of two FBI Alerts in 2018.
_500_344.png) And, according to AlienVault Labs, the methods used by SamSam are more akin to a targeted attack than typical opportunistic ransomware. SamSam attacks also seem to go in waves. One of the most notable was a spring 2018 hit on a large New York hospital which publicly declined to pay the attacker’s $44,000 ransomware demand. It took a month for the hospital’s IT system to be fully restored.
SamSam attackers are known to:
Gain remote access through traditional attacks, such as JBoss exploits
Deploy web-shells
Connect to RDP over HTTP tunnels such as ReGeorg
Run batch scripts to deploy the ransomware over machines
SamSam isn’t going away either. AlienVault Labs has seen recent variants. You might want to read more about the threat actors behind SamSam, their methods of attacks, and recommendations for heading
And, according to AlienVault Labs, the methods used by SamSam are more akin to a targeted attack than typical opportunistic ransomware. SamSam attacks also seem to go in waves. One of the most notable was a spring 2018 hit on a large New York hospital which publicly declined to pay the attacker’s $44,000 ransomware demand. It took a month for the hospital’s IT system to be fully restored.
SamSam attackers are known to:
Gain remote access through traditional attacks, such as JBoss exploits
Deploy web-shells
Connect to RDP over HTTP tunnels such as ReGeorg
Run batch scripts to deploy the ransomware over machines
SamSam isn’t going away either. AlienVault Labs has seen recent variants. You might want to read more about the threat actors behind SamSam, their methods of attacks, and recommendations for heading |
Threat | Wannacry APT 19 APT 18 APT 22 APT 23 | ||
| 2018-10-30 00:08:00 | Google launches reCAPTCHA v3 that detects bad traffic without user interaction (lien direct) | reCAPTCHA v3 assigns incoming site visitors a risk score and lets webmasters takes custom actions based on this score. | APT 19 | |||
| 2018-10-29 17:00:00 | MadoMiner Part 2 - Mask (lien direct) |
This is a guest post by independent security researcher James Quinn.
If you have not yet read the first part of the MadoMiner analysis, please do so now. This analysis will pick up where Part 1 left off, while also including a brief correction. The x64 version of the Install module was listed as identical to the x86 Install module. However, this is not correct. The x64 Install module is identical in run-through to the 360Safe.exe module, which will be discussed later in this analysis.
In addition, take care with this portion of the malware. The batch script for Mask.exe, DemC.bat, appears to run if it detects any copies of itself during runtime, or if you run the x64 version of install on a 32 bit machine.
Where Install.exe was in charge of infecting new victims with MadoMiner, it seems Mask.exe is where the real payoff lies. Mask.exe utilizes XMRig miners in order to mine for XMR which it then sells for profit. While madominer was earning $6,000 a month as of the last analysis,
 Around 10/14, MineXMR closed the old address due to botnet reports. A new address has been identified at 47QrUBQ4ejMW5wrWXiKUyRcQCZszauGWg9c3SLkzFoBJi45M5yN6gVPjVxSUfjMq4u8vepEejdnxyRQcv4RuFGy25x67433, mining through minexmr.com again. Currently, the hashrate is at 109Kh/s, and steadily rising.
Around 10/14, MineXMR closed the old address due to botnet reports. A new address has been identified at 47QrUBQ4ejMW5wrWXiKUyRcQCZszauGWg9c3SLkzFoBJi45M5yN6gVPjVxSUfjMq4u8vepEejdnxyRQcv4RuFGy25x67433, mining through minexmr.com again. Currently, the hashrate is at 109Kh/s, and steadily rising.
 Also, around the time that the address changed, MadoMiner also became drastically different.
Malware Analysis
Where Install.exe only downloaded 1 file from a remote host, Mask.exe downloads two files. In addition, the servers used to download the files are also different than Install.exe, increasing the proposed size of the botnet.
Also, around the time that the address changed, MadoMiner also became drastically different.
Malware Analysis
Where Install.exe only downloaded 1 file from a remote host, Mask.exe downloads two files. In addition, the servers used to download the files are also different than Install.exe, increasing the proposed size of the botnet.
 Domains
In addition to the 2 domains identified in part 1, a new domain has also been identified for a distribution server:
http://d.honker[dot]info
However, the domain is currently dead. In addition, the mining server currently used is pool.minexmr[dot]com
A C2 server(newly updated version):
http://qq.honker[dot]info
Previously identified distribution domains:
http://da[dot]alibuf.com:3/
http://bmw[dot]hobuff.info:3/
Previously Identified IPs:
61.130.31.174
Previously identified mining servers:
http://gle[dot]freebuf.info
http://etc[dot]freebuf.info
http://xmr[dot]freebuf.info
http://xt[dot]freebuf.info
http://boy[dot]freebuf.info
http://liang[dot]alibuf.com
http://dns[dot]alibuf.com
http://x[dot]alibuf.com
In addition, http://da[dot]alibuf.com:3, the main distribution server, seems to have been registered by bodfeo[at]hotmail.com in early October 2017. According to an analysis by Steve Butt of DomainTools, this email was linked to APT19/c0d0s0, however it was most likely due to domain reselling.
Exploits
During the execution Domains
In addition to the 2 domains identified in part 1, a new domain has also been identified for a distribution server:
http://d.honker[dot]info
However, the domain is currently dead. In addition, the mining server currently used is pool.minexmr[dot]com
A C2 server(newly updated version):
http://qq.honker[dot]info
Previously identified distribution domains:
http://da[dot]alibuf.com:3/
http://bmw[dot]hobuff.info:3/
Previously Identified IPs:
61.130.31.174
Previously identified mining servers:
http://gle[dot]freebuf.info
http://etc[dot]freebuf.info
http://xmr[dot]freebuf.info
http://xt[dot]freebuf.info
http://boy[dot]freebuf.info
http://liang[dot]alibuf.com
http://dns[dot]alibuf.com
http://x[dot]alibuf.com
In addition, http://da[dot]alibuf.com:3, the main distribution server, seems to have been registered by bodfeo[at]hotmail.com in early October 2017. According to an analysis by Steve Butt of DomainTools, this email was linked to APT19/c0d0s0, however it was most likely due to domain reselling.
Exploits
During the execution |
APT 19 | |||
| 2018-10-19 15:30:05 | (Déjà vu) Oceansalt Cyberattack Wave Linked To Defunct Chinese APT Comment Crew (lien direct) | News broke today that newly discovered first-stage implant targeting Korean-speaking victims borrows code from another reconnaissance tool linked to Comment Crew, a Chinese nation-state threat actor that was exposed in 2013 following cyber espionage campaigns against the United States. Dubbed Oceansalt, the threat has been spotted on machines in South Korea, the United States, and Canada. … The ISBuzz Post: This Post Oceansalt Cyberattack Wave Linked To Defunct Chinese APT Comment Crew | Tool Threat | APT 32 APT 1 | ||
| 2018-10-19 07:06:03 | Attackers behind Operation Oceansalt reuse code from Chinese Comment Crew (lien direct) | Security researchers from McAfee have recently uncovered a cyber espionage campaign, tracked as Operation Oceansalt, targeting South Korea, the United States, and Canada. The threat actors behind Operation Oceansalt are reusing malware previously associated with China-linked cyberespionage group APT1. “McAfee Advanced Threat Research and Anti-Malware Operations teams have discovered another unknown data reconnaissance implant targeting Korean-speaking users.” reads the report. “We […] | Malware Threat | APT 32 APT 1 | ||
| 2018-10-18 19:17:05 | New APT Could Signal Reemergence of Notorious Comment Crew (lien direct) | A custom malware used in a five-pronged APT espionage campaign was largely built from the defunct Comment Crew's proprietary code. | Malware | APT 1 | ||
| 2018-10-18 04:01:00 | The Mysterious Return of Years-Old APT1 Malware (lien direct) | Security researchers have discovered a new instance code associated with APT1, a notorious Chinese hacking group that disappeared in 2013. | Malware | APT 1 | ||
| 2018-10-18 04:01:00 | Oceansalt cyberattack wave linked to defunct Chinese APT Comment Crew (lien direct) | The source code of malware from the ancient Chinese military-affiliated group appears to have changed hands. | Malware | APT 32 APT 1 | ||
| 2018-10-18 00:01:00 | New Reconnaissance Tool Uses Code from Eight-Year-Old Comment Crew Implant (lien direct) | A newly discovered first-stage implant targeting Korean-speaking victims borrows code from another reconnaissance tool linked to Comment Crew, a Chinese nation-state threat actor that was exposed in 2013 following cyber espionage campaigns against the United States. [...] | Tool Threat | APT 1 | ||
| 2018-10-03 17:00:00 | DHS aware of ongoing APT attacks on cloud service providers (lien direct) | Attacks most likely linked to APT10, a Chinese cyber-espionage group, also known as Red Apollo, Stone Panda, POTASSIUM, or MenuPass. | APT 10 | |||
| 2018-09-23 14:33:04 | Fuite de données corrigée pour Info Greffe (lien direct) | Une fuite de données colmatée pour le site Info Greffe. Il était possible d'accéder aux factures des clients sans avoir besoin d’être authentifié. Le site Info Greffe permet d’accéder à l’information légale sur les entreprises. Dirigeant, greffe, formalité, … Une fuite permet... Cet article Fuite de données corrigée pour Info Greffe est apparu en premier sur ZATAZ. | APT 15 | |||
| 2018-09-15 08:34:01 | China-linked APT10 group behind new attacks on the Japanese media sector (lien direct) | Recently researchers from FireEye uncovered and blocked a campaign powered by the Chinese APT10 cyber espionage group aimed at Japanese media sector In July, security researchers from FireEye uncovered and blocked a campaign carried out by Chinese APT10 group (aka Menupass, and Stone Panda) aimed at Japanese media sector. Experts noticed the group since around […] | APT 10 | |||
| 2018-09-14 17:23:01 | China-linked APT10 Hackers Update Attack Techniques (lien direct) | Recently attacks launched by the China-linked threat actor APT10 against the Japanese media sector revealed the use of updated tactics, techniques and procedures (TTPs), FireEye says. | Threat | APT 10 | ||
| 2018-09-13 11:00:00 | APT10 ciblant les sociétés japonaises à l'aide de TTPS mis à jour APT10 Targeting Japanese Corporations Using Updated TTPs (lien direct) |
Introduction
En juillet 2018, les appareils FireEye ont détecté et bloqué ce qui semble être une activité APT10 (Menupass) ciblant le secteur des médias japonais.APT10 est un groupe de cyber-espionnage chinois que Fireeye a suivi depuis 2009, et ils ont une histoire de ciblant les entités japonaises .
Dans cette campagne, le groupe a envoyé des e-mails de phishing de lance contenant des documents malveillants qui ont conduit à l'installation de la porte dérobée Uppercut.Cette porte dérobée est bien connue dans la communauté de la sécurité comme Anel , et il venait en bêta ou en RC (candidat à la libération) jusqu'à récemment.Une partie de cet article de blog discutera du
Introduction In July 2018, FireEye devices detected and blocked what appears to be APT10 (Menupass) activity targeting the Japanese media sector. APT10 is a Chinese cyber espionage group that FireEye has tracked since 2009, and they have a history of targeting Japanese entities. In this campaign, the group sent spear phishing emails containing malicious documents that led to the installation of the UPPERCUT backdoor. This backdoor is well-known in the security community as ANEL, and it used to come in beta or RC (release candidate) until recently. Part of this blog post will discuss the |
Technical | APT 10 APT 10 | ★★★★ | |
| 2018-09-10 18:59:03 | Chinese LuckyMouse APT has been using a digitally signed network filtering driver in recent attacks (lien direct) | Security experts observed the LuckyMouse APT group using a digitally signed 32- and 64-bit network filtering driver NDISProxy in recent attacks. Security experts from Kaspersky have observed the LuckyMouse APT group (aka Emissary Panda, APT27 and Threat Group 3390) using a digitally signed 32- and 64-bit network filtering driver NDISProxy in recent attacks. The APT group […] | Threat | APT 27 APT 1 | ★★★ | |
| 2018-09-03 12:49:03 | APT10 Under Close Scrutiny as Potentially Linked to Chinese Ministry of State Security (lien direct) | An advanced threat actor has been associated with China's Ministry of State Security via two individuals and a Chinese firm. | Threat | APT 10 | ||
| 2018-08-02 15:11:04 | The Year Targeted Phishing Went Mainstream (lien direct) | A story published here on July 12 about a new sextortion-based phishing scheme that invokes a real password used by each recipient has become the most-read piece on KrebsOnSecurity since this site launched in 2009. And with good reason -- sex sells (the second most-read piece here was my 2015 scoop about the Ashley Madison hack). But beneath the lurid allure of both stories lies a more unsettling reality: It has never been easier for scam artists to launch convincing, targeted phishing and extortion scams that are automated on a global scale. And given the sheer volume of hacked and stolen personal data now available online, it seems almost certain we will soon witness many variations on these phishing campaigns that leverage customized data elements to enhance their effectiveness. | APT 15 | |||
| 2018-07-31 14:03:05 | Google Chrome launches on Daydream headsets, could make enterprise VR training a reality (lien direct) | Google Chrome is now accessible for Daydream View and the Lenovo Mirage Solo, which could transform business training techniques. | APT 15 | |||
| 2018-07-20 13:00:00 | Things I Hearted this Week, 20th July 2018 (lien direct) |
INFOSEC RECRUITING - IS THE INDUSTRY CREATING ITS OWN DROUGHT
We've all been blasted with many a report that infosec has a massive skills gap. But what if the problem doesn't lie with the lack of skilled professionals, but the hiring process itself?
Thomas Fischer makes a compelling argument, using some of his personal recent experiences from both sides of the hiring process.
InfoSec Recruiting – Is the Industry Creating its own Drought? | Liquid Matrix
GDPR
Did you think that discussions around GDPR were over? You thought wrong.
Want to avoid GDPR fines? Adjust your IT Procurement methods | HelpNetSecurity
SEXTORTION SCAMS
 A clever new twist on an on extortion email scam includes a password the recipient previously used at a hacked website, to lend credence to claims that the sender has hacked the recipients computer / webcam and recorded embarrassing videos.
Sextortion Scam Uses Recipient’s Hacked Passwords | Krebs on Security
TESLA
Elon Musk continues to make the headlines, sometimes for the right, and other times for the wrong reasons. But it's worth taking a look at the companies security. While there was the infamous emaila few weeks back where Musk pointed the finger of blame to a rogue employee, it's not the first case of cybersecurity gone wrong in the company.
Tesla sued an oil-industry executive for impersonating Musk in an email. The tricksters goal was to undermine tesla's energy-efficient transportation.
Here’s why Tesla has been sabotaged twice in two years — lax network security | Last Watchdog
A clever new twist on an on extortion email scam includes a password the recipient previously used at a hacked website, to lend credence to claims that the sender has hacked the recipients computer / webcam and recorded embarrassing videos.
Sextortion Scam Uses Recipient’s Hacked Passwords | Krebs on Security
TESLA
Elon Musk continues to make the headlines, sometimes for the right, and other times for the wrong reasons. But it's worth taking a look at the companies security. While there was the infamous emaila few weeks back where Musk pointed the finger of blame to a rogue employee, it's not the first case of cybersecurity gone wrong in the company.
Tesla sued an oil-industry executive for impersonating Musk in an email. The tricksters goal was to undermine tesla's energy-efficient transportation.
Here’s why Tesla has been sabotaged twice in two years — lax network security | Last Watchdog
|
Tesla APT 1 | |||
| 2018-06-27 06:14:00 | Reduce breach risk and costs with security resilience (lien direct) | In cybersecurity circles, there's a common axiom that states, “There are two types of companies: those that have been breached and those that don't know they have been breached.” If the phrase sounds of doom and gloom, it's meant to be because the harsh reality is that almost every company will suffer a cybersecurity breach. Businesses can spend and spend on the latest and greatest security technology and still get breached for a number of reasons, including user-related issues. The challenge for businesses is to find the breach as soon as possible and return to normal operations as quickly as possible. [ Find out how 4 deception tools deliver truer network security. | Get the latest from CSO by signing up for our newsletters. ] | APT 17 | |||
| 2018-06-25 15:03:20 | Bejtlich on the APT1 Report: No Hack Back (lien direct) |  Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted: Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted:  In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, |
Hack | APT 1 | ||
| 2018-06-19 21:58:03 | APT15 Pokes Its Head Out With Upgraded MirageFox RAT (lien direct) | This is the first evidence of the China-linked threat actor's activity since hacked the U.K. government and military in 2017 (which wasn't made public until 2018). | APT 15 | |||
| 2018-06-18 12:41:02 | China-Linked APT15 is still very active, experts found its new malware tracked as \'MirageFox\' (lien direct) | Following the recent hack of a US Navy contractor security experts found evidence of very recent activity by the China-linked APT group tracked as APT15. The China-linked APT15 group (aka Ke3chang, Mirage, Vixen Panda, Royal APT and Playful Dragon) has developed a new strain of malware borrowing the code from one of the tool he used in past […] | APT 15 APT 25 | |||
| 2018-06-18 04:38:03 | China-Linked APT15 Develops New \'MirageFox\' Malware (lien direct) | A cyber-espionage group believed to be operating out of China has developed a new piece of malware that appears to be based on one of the first tools used by the threat actor. | APT 15 | |||
| 2018-06-14 06:23:04 | China-linked Emissary Panda APT group targets National Data Center in Asia (lien direct) | A China-linked APT group, LuckyMouse, Emissary Panda, APT27 and Threat Group 3390, has targeted a national data center in Central Asia. The APT group has been active since at least 2010, the crew targeted U.S. defense contractors and financial services firms worldwide. In March 2018, security experts at Kaspersky Lab have observed an attack powered by the […] | APT 27 APT 1 | |||
| 2018-05-05 12:13:02 | New Service Blocks EU Users So Companies Can Save Thousands on GDPR Compliance (lien direct) | A new service called GDPR Shield is making the rounds this week and for all the wrong reasons. The service, advertised as a piece of JavaScript that webmasters embed on their sites, blocks EU-based users from accessing a website, just so the parent company won't have to deal with GDPR compliance. [...] | APT 19 | |||
| 2018-05-03 14:35:04 | Facebook\'s Phishing Detection Tool Now Recognizes Homograph Attacks (lien direct) | Facebook has updated a phishing detection toolkit it developed two years ago. The update now allows webmasters who sign up for the tool to detect homograph (Unicode-based lookalike) domains created for their websites. [...] | APT 19 | |||
| 2018-03-26 13:00:00 | Explain PGP Encryption: An Operational Introduction (lien direct) |
 If you don’t already know what Pretty Good Privacy (PGP) is; you may have heard of PGP before, perhaps during a discussion on how to secure your communications, or perhaps in one of those how-to maintain privacy guides. PGP is a popular solution for encrypting, decrypting, signing, and verifying messages and files, often found in email communications and package repository identity verification (because security matters).
Most generic guides simply explain PGP at a high-level or how to encrypt and decrypt messages using specific software, and not much more than that. The goal of this introduction to PGP is to illustrate a more timeless and operational approach to using PGP safely, with respect to both information security and operational security.
Firstly, we introduce PGP theoretically and practically, this means understanding how PGP works and what we can actually do with PGP. To better understand our security stance, we assess the CIA Triad, a theoretical Information Security model, that considers the confidentiality, integrity, and availability of information. Next, we get familiar with our threat model (similar to OPSEC Model); in this step, we analyze personalized risks and threats. To mitigate any identified threats and reduce risk, we implement operational security practices.
At a more concise glance, we will discuss the following:
PGP, OpenPGP & GPG
Public & Private Key Pairs
Information Security (CIA Triad)
Confidentiality: message encryption, information storage
Integrity: message/file authenticity, web of trust
Availability: key servers, web of trust, metadata
Assessing Threats & Risk
Threat Modeling
Operational Security
Clients & Use Guides: Windows, Linux, Mac, Web
With that caveat in mind, let’s jump straight in.
PGP, OpenPGP & GPG: What is it?
PGP is a protocol used for encrypting, decrypting and signing messages or files using a key pair. PGP is primarily used for encrypting communications at the Application layer, typically used for one-on-one encrypted messaging. You may find yourself needing to use PGP if you want to be certain that only the intended receiver can access your private message, thwarting the efforts of intercepting parties, or if you just want to verify the sender’s identity.
There are different variations of PGP: OpenPGP, PGP and GPG, but they generally all do the same thing. Here is the quick terminology run-down:
PGP: Pretty Good Privacy, original proprietary protocol. Released in 1991.
OpenPGP: Pretty Good Privacy, but it is an open-source version, and it has become the universally-accepted PGP standard. Released in 1997.
GPG: GNU Privacy Guard, another popular solution that follows OpenPGP standards. Released in 1999.
When someone says PGP, it is generally s
If you don’t already know what Pretty Good Privacy (PGP) is; you may have heard of PGP before, perhaps during a discussion on how to secure your communications, or perhaps in one of those how-to maintain privacy guides. PGP is a popular solution for encrypting, decrypting, signing, and verifying messages and files, often found in email communications and package repository identity verification (because security matters).
Most generic guides simply explain PGP at a high-level or how to encrypt and decrypt messages using specific software, and not much more than that. The goal of this introduction to PGP is to illustrate a more timeless and operational approach to using PGP safely, with respect to both information security and operational security.
Firstly, we introduce PGP theoretically and practically, this means understanding how PGP works and what we can actually do with PGP. To better understand our security stance, we assess the CIA Triad, a theoretical Information Security model, that considers the confidentiality, integrity, and availability of information. Next, we get familiar with our threat model (similar to OPSEC Model); in this step, we analyze personalized risks and threats. To mitigate any identified threats and reduce risk, we implement operational security practices.
At a more concise glance, we will discuss the following:
PGP, OpenPGP & GPG
Public & Private Key Pairs
Information Security (CIA Triad)
Confidentiality: message encryption, information storage
Integrity: message/file authenticity, web of trust
Availability: key servers, web of trust, metadata
Assessing Threats & Risk
Threat Modeling
Operational Security
Clients & Use Guides: Windows, Linux, Mac, Web
With that caveat in mind, let’s jump straight in.
PGP, OpenPGP & GPG: What is it?
PGP is a protocol used for encrypting, decrypting and signing messages or files using a key pair. PGP is primarily used for encrypting communications at the Application layer, typically used for one-on-one encrypted messaging. You may find yourself needing to use PGP if you want to be certain that only the intended receiver can access your private message, thwarting the efforts of intercepting parties, or if you just want to verify the sender’s identity.
There are different variations of PGP: OpenPGP, PGP and GPG, but they generally all do the same thing. Here is the quick terminology run-down:
PGP: Pretty Good Privacy, original proprietary protocol. Released in 1991.
OpenPGP: Pretty Good Privacy, but it is an open-source version, and it has become the universally-accepted PGP standard. Released in 1997.
GPG: GNU Privacy Guard, another popular solution that follows OpenPGP standards. Released in 1999.
When someone says PGP, it is generally s |
APT 15 | |||
| 2018-03-13 16:16:02 | China-Linked APT15 Used Myriad of New Tools To Hack UK Government Contractor (lien direct) | Cyber espionage group APT15 is back, this time stealing sensitive data from a UK government contractor. | APT 15 | |||
| 2018-03-12 18:07:04 | China-Linked APT15 used new backdoors in attack against UK Government\'s service provider (lien direct) | China-Linked APT15 used new backdoors is an attack that is likely part of a wider operation aimed at contractors at various UK government departments and military organizations. Last week Ahmed Zaki, a senior malware researcher at NCC Group, presented at the Kaspersky's Security Analyst Summit (SAS), details of a malware-based attack against the service provider for the […] | APT 15 | |||
| 2018-03-02 05:51:02 | New Tools Make Checking for Leaked Passwords a Lot Easier (lien direct) | The work that Australian security researcher Troy Hunt has done with the Have I Been Pwned project is yielding useful tools that developers and webmasters can now use to make sure users stop using silly and easy to guess passwords. [...] | APT 19 | |||
| 2018-02-28 21:54:40 | NBlog March 1 - Invasion of the Cryptominers (lien direct) |  That's it, we're done! The 2018 malware awareness module is on its way to NoticeBored subscribers, infecting customers with ... our passion for the topic.There are 28 different types of awareness and training material, in three parallel streams as always: Stream A: security awareness materials for staff/all employees [if !supportLists]-->1. [endif]-->Train-the-trainer guide on malware MS Word document [if gte vml 1]> That's it, we're done! The 2018 malware awareness module is on its way to NoticeBored subscribers, infecting customers with ... our passion for the topic.There are 28 different types of awareness and training material, in three parallel streams as always: Stream A: security awareness materials for staff/all employees [if !supportLists]-->1. [endif]-->Train-the-trainer guide on malware MS Word document [if gte vml 1]> |
Malware | APT 15 | ||
| 2018-02-18 18:58:01 | Fuite des adresses mails des clients pour le site Info greffe (lien direct) | Le site Info Greffe souffre d’un problème de conception. Un bug qui permet de mettre la main sur l’ensemble des adresses électroniques des clients. La CNIL alertée. Un lien Info Greffe … et c’est le bug ! Premièrement, je n’expliquerai pas pour le moment, comment un pir... Cet article Fuite des adresses mails des clients pour le site Info greffe est apparu en premier sur ZATAZ. | APT 15 | |||
| 2018-02-06 14:00:00 | Debunking these 3 Domain Name Registration Myths Once and For All (lien direct) |
Let’s be honest:
Domain names suck.
It’s a pain to come up with possible variations. It’s time-consuming to sift through which are available (none are). And going through the process of buying an unavailable one is about as much fun as a root canal.
But there’s a reason they’re such a hassle. There’s a lot riding on them. There’s a massive difference between a good one and a great one.
Many times, that difference is millions or billions. That sounds like an exaggeration, but it’s not. Here’s why.
Myth #1. Domain Registrations Increase SEO
Exact match domains (EMDs) used to be a thing (or still are, depending on who you talk to). You stuffed a few keywords into the domain before checkout to give yourself that extra edge to rank for cut-throat queries like “bestvitaminshop.com.”
Domain age has also been rumored to influence rankings. Somehow, the older the domain and the longer you register it for tells Google… to like you more?
Admittedly, the logic is flimsy.
But Google originally debunked these myths in 2009, according to some digging by Matt McGee at Search Engine Land.
First, they had a Google Webmaster Help forum thread where Googler, John Mueller, addressed this question head-on:
“A bunch of TLDs do not publish expiration dates — how could we compare domains with expiration dates to domains without that information? It seems that would be pretty hard, and likely not worth the trouble. Even when we do have that data, what would it tell us when comparing sites that are otherwise equivalent? A year (the minimum duration, as far as I know) is pretty long in internet-time :-).”
Next up, they had former Google PR chief, Matt Cutts, on the record several times addressing this issue:
“To the best of my knowledge, no search engine has ever confirmed that they use length-of-registration as a factor in scoring. If a company is asserting that as a fact, that would be troubling.”
So there you have it. “Officially,” domain registrations don’t affect SEO. At least, not directly.
Recently, there’s some evidence that search engine result page (SERP) click-through rate (CTR) affects rankings. One experiment had a sizable group of people click on a random listing in the seventh position to see what (if any) changes occurred.
And within just a few hours? Straight to the top.
 (image source)
The finding shows an odd correlation between SERP performance and its influence on ranks. The point of this being that it is possible that a better domain name, one that’s more credible and interesting for people to click, could indirectly influence rankings.
The industry standard .com domain is still seen as the most credible, even though new top-level domains (TLDs) continue to pop up and gain acceptance. Studies have backed this up, showing that .com domains generally dr
(image source)
The finding shows an odd correlation between SERP performance and its influence on ranks. The point of this being that it is possible that a better domain name, one that’s more credible and interesting for people to click, could indirectly influence rankings.
The industry standard .com domain is still seen as the most credible, even though new top-level domains (TLDs) continue to pop up and gain acceptance. Studies have backed this up, showing that .com domains generally dr |
APT 19 | |||
| 2018-01-30 13:40:00 | OTX Trends Part 3 - Threat Actors (lien direct) |
By Javvad Malik and Chris Doman
This is the third of a three part series on trends identified by AlienVault in 2017.
Part 1 focused on exploits and part 2 addressed malware. This part will discuss threat actors and patterns we have detected with OTX.
Which threat actors should I be most concerned about?
Which threat actors your organization should be most concerned about will vary greatly. A flower shop will have a very different threat profile from a defense contractor. Therefore below we’ve limited ourselves to some very high level trends of particular threat actors below- many of which may not be relevant to your organisation.
Which threat actors are most active?
The following graph describes the number of vendor reports for each threat actor over the past two years by quarter:
 For clarity, we have limited the graph to the five threat actors reported on most in OTX. This is useful as a very rough indication of which actors are particularly busy.
Caveats
There are a number of caveats to consider here. One news-worthy event against a single target may be reported in multiple vendor reports. Whereas a campaign against thousands of targets may be only represented by one report.
Vendors are also more inclined to report on something that is “commercially interesting”. For example activity targeting banks in the United States is more likely to be reported than attacks targeting the Uyghur population in China. It’s also likely we missed some reports, particularly in the earlier days of OTX which may explain some of the increase in reports between 2016 and 2017.
The global targeted threat landscape
There are a number of suggested methods to classify the capability of different threat actors. Each have their problems however. For example – if a threat actor never deploys 0-day exploits do they lack the resources to develop them, or are they mature enough to avoid wasting resources unnecessarily?
Below we have plotted out a graph of the threat actors most reported on in the last two years. We have excluded threat actors whose motivation is thought to be criminal, as that wouldn’t be an apples to apples comparison.
Both the measure of their activity (the number of vendor reports) and the measure of their capability (a rough rule of thumb) are not scientific, but can provide some rough insights:
For clarity, we have limited the graph to the five threat actors reported on most in OTX. This is useful as a very rough indication of which actors are particularly busy.
Caveats
There are a number of caveats to consider here. One news-worthy event against a single target may be reported in multiple vendor reports. Whereas a campaign against thousands of targets may be only represented by one report.
Vendors are also more inclined to report on something that is “commercially interesting”. For example activity targeting banks in the United States is more likely to be reported than attacks targeting the Uyghur population in China. It’s also likely we missed some reports, particularly in the earlier days of OTX which may explain some of the increase in reports between 2016 and 2017.
The global targeted threat landscape
There are a number of suggested methods to classify the capability of different threat actors. Each have their problems however. For example – if a threat actor never deploys 0-day exploits do they lack the resources to develop them, or are they mature enough to avoid wasting resources unnecessarily?
Below we have plotted out a graph of the threat actors most reported on in the last two years. We have excluded threat actors whose motivation is thought to be criminal, as that wouldn’t be an apples to apples comparison.
Both the measure of their activity (the number of vendor reports) and the measure of their capability (a rough rule of thumb) are not scientific, but can provide some rough insights:
 A rough chart of the activity and capability of notable threat actors in the last year
Perhaps most notable here is which threat actors are not listed here. Some, such as APT1 and Equation Group, seem to have disappeared under their existing formation following from very public reporting. It seems unlikely groups which likely employ thousands of people such as those have disappeared completely. The lack of such reporting is more likely a result of significantly changed tactics and identification following their outing. Others remain visibly active, but not enough to make our chart of “worst offenders”.
A review of the most reported on threat actors
The threat actor referenced i
A rough chart of the activity and capability of notable threat actors in the last year
Perhaps most notable here is which threat actors are not listed here. Some, such as APT1 and Equation Group, seem to have disappeared under their existing formation following from very public reporting. It seems unlikely groups which likely employ thousands of people such as those have disappeared completely. The lack of such reporting is more likely a result of significantly changed tactics and identification following their outing. Others remain visibly active, but not enough to make our chart of “worst offenders”.
A review of the most reported on threat actors
The threat actor referenced i |
APT 38 APT 28 APT 10 APT 3 APT 1 APT 34 | |||
| 2018-01-14 14:08:40 | Remembering When APT Became Public (lien direct) | 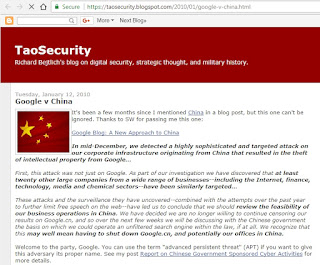 Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for |
APT 17 APT 1 | |||
| 2017-12-13 10:05:21 | Google Releases an Updated SEO Starter Guide (lien direct) | After many years, Google has finally released an updated version of their SEO Starter Guide. This guide is a resource for webmasters that contains Google's recommendations on how to make sure web sites are search-engine-friendly. [...] | APT 19 | |||
| 2017-12-05 08:24:37 | NBlog December 5 - lurid headline (lien direct) | Social-Engineer.com's newsletter is a useful source of information about social engineering methods. The latest issue outlines some of the tricks used by phishers to lure their victims initially."It is not breaking news that phishing is the leading cause of data breaches in the modern world. It is safe to ask why that is the case though, given how much of this email gets caught up in our spam filters and perimeter defenses. One trick sophisticated attackers use is triggering emotional responses from targets using simple and seemingly innocuous messaging to generate any response at all. Some messaging does not initially employ attachments or links, but instead tries to elicit an actual reply from the target. Once the attackers establish a communication channel and a certain level of trust, either a payload of the attacker's choosing can then be sent or the message itself can entice the target to act."That same technique is used by advertisers over the web in the form of lurid or intriguing headlines and images, carefully crafted to get us to click the links and so dive into a rabbit warren of further items and junk, all the while being inundated with ads. You may even see the lures here or hereabouts (courtesy of Google). Once you've seen enough of them, you'll recognize the style and spot the trigger words - bizarre, trick, insane, weird, THIS and so on, essentially meaning CLICK HERE, NOW!They are curiously attractive, almost irresistible, even though we've groped around in the rabbit warrens before and suspect or know what we're letting ourselves in for. But why is that? 'Curiously' is the key: it's our natural curiosity that leads us in. It's what led you to read this sentence. Ending the previous paragraph with a rhetorical question was my deliberate choice. Like magpies or trout chasing something shiny, I got you. You fell for it. I manipulated you. Sorry.There are loads more examples along similar lines - random survey statistics for instance ("87% of X prone to Y") and emotive subjects ("Doctors warn Z causes cancer"). We have the newspapers to thank for the very term 'headline', not just the tabloid/gutter press ("Elvis buried on Mars") but the broadsheets and more up-market magazines and journals, even scientific papers. The vast majority of stuff we read has titles and headings, large and bold in style, both literally and figuratively. Postings on this blog all have short titles and a brief summary/description, and some of the more detailed pieces have subheadings providing structure and shortcuts for readers who lack the time or inclination to read every word ... which hints at another issue, information overload. Today's Web is so vast that we're all sipping from the fire hose.And that | Guideline | APT 15 | ||
| 2017-11-02 09:19:30 | WordPress patches SQL injection bug in security release (lien direct) | Webmasters should update immediately to prevent website takeovers. | APT 19 |
To see everything:
Our RSS (filtrered)
